Stepping into Security Assessments Part 2
[glossary_exclude]Stepping into Security Assessments – Metrics & Executive Engagement
Part II in the Series
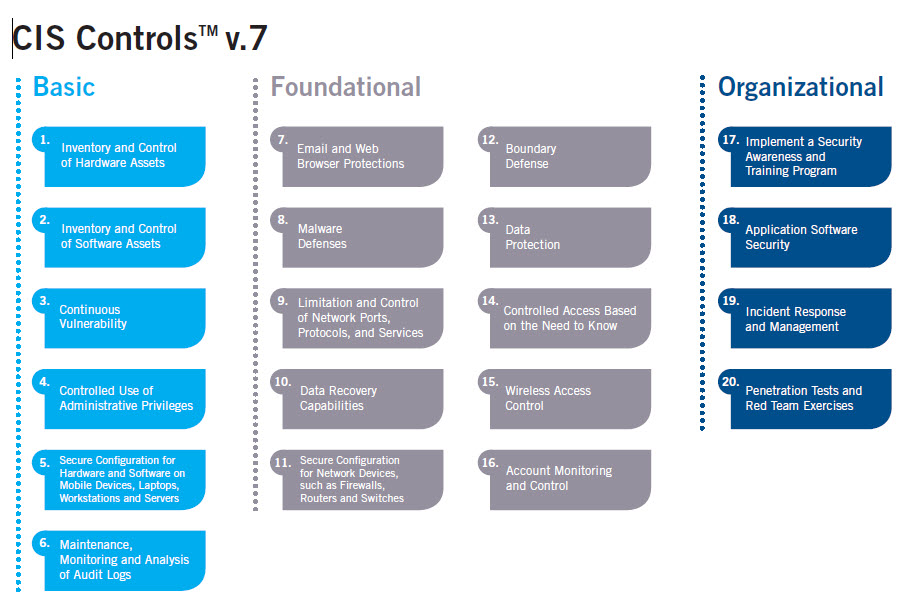
Before jumping into the topic of assessment metrics, first, a quick update regarding the Center for Internet Security (CIS) controls. Recently released Version 7 separates the 20 controls into three groups: Basic (1-6), Foundational (7-16) and Organizational (17-20) as depicted in the featured image graphic.
These three groupings aid the organization in prioritizing the activities associated with the controls. Basic Controls are key for all types of organizations and should be implemented to ensure cyber defense is in place. Foundational Controls are the next step. They are technical in nature and implementing Best Practices will provide significant enhancement of cyber-security posture. The Organizational Controls embody some technical aspects; however, they are higher level and primarily focused on people and process.
Security Assessments are conducted in the context of one or more frameworks. As discussed in Part 1 (in our previous issue), common frameworks include:
- CIS controls (above)
- The more comprehensive NIST Cybersecurity Framework; and for Cloud computing
- Cloud Security Alliance’s Cloud Controls Matrix
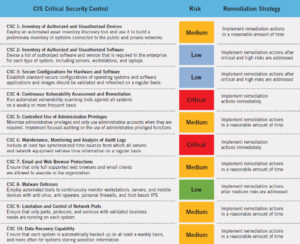
The purpose of a Security Assessment is to measure the organization’s cyber-security readiness. Initially, the application of metrics to this task can seem dauntingly complex. For example, looking at the first CIS control “Inventory and Control of Hardware Assets,” assessment metrics could include sigma level (1-6) compliance rankings for the following sub-controls:
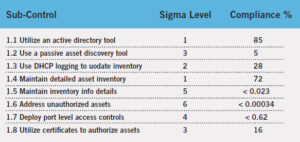
Keeping in mind that this table represents the measured results for only Basic Control One, it is easy to imagine that the tabular presentation of sigma compliance metrics for all 20 CIS controls could result in an overwhelming amount of mind-numbing data. Therefore, it is clear Security Assessment control compliance must not only be measured, but that the resulting metrics must be presented in a manner which conveys the prioritized “important” information to a non-technical audience, while at the same time preserving the detailed data for actionable analysis by the technical team.
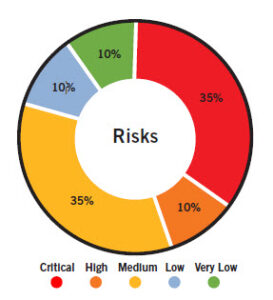
This can be accomplished using graphics to represent comparative risk levels.
Another way Security Assessment metrics can be presented is in a radar chart. In this chart, the twenty CIS controls are ranked based on the people (employees) who have been properly trained to participate in the control activities. Note that Security Assessments also take into account the individual’s job descriptions to ensure that even if the employees are trained, they also have the available time required to perform the defined tasks consistently.
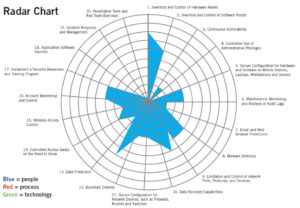
Security Assessment results can be visualized using an Infographic to summarize the overall all security posture (see chart above.)
Security Assessment Metrics can also be evaluated by looking at which part of the assessment they are associated with. The metrics for a Penetration Test will be much different than the metrics resulting from a Security Skills Assessment. The bottom line is that Assessment metrics must be presented in a manner that is appropriate for the audience. This leads to another key point: executive engagement.
It is fundamentally important that the executive team be an active participant in the Security Assessment planning and review process.
C-level executives have a fiduciary duty to the organization to protect corporate assets and therefore it is imperative that they are participants in the organization’s security posture. Another important issue is that the findings of the Security Assessment may not be acted on unless the executive team agrees to prioritize the remediation activities. Presentation of Security Assessment metrics in an easy to understand format that conveys the important information efficiently will ensure executive team support.
It is important to select the most appropriate framework for your Security Assessment, to involve the C-suite, and that the results are presented in a manner that is tailored to specific audiences. If these guidelines are followed, your Security Assessment will provide actionable insights that, if acted upon, will help keep your organization’s information assets secure. [/glossary_exclude]
recent posts
You may already have a formal Data Governance program in […]