New Network Monitoring Tool Addresses Massive Data Volumes
[glossary_exclude]The volume of network traffic inside today’s corporate environments is staggering. Monitoring this increasingly large volume of traffic for signs of malicious activity can be an overwhelmingly complex task. One strategy to deal with this situation is the implementation of technology that copies mirrored data to remote locations for archival, analysis, and potential use in future forensic investigations.
ERSPAN ADDS LAYER 3 ROUTING TO NETWORK TRAFFIC ANALYSIS
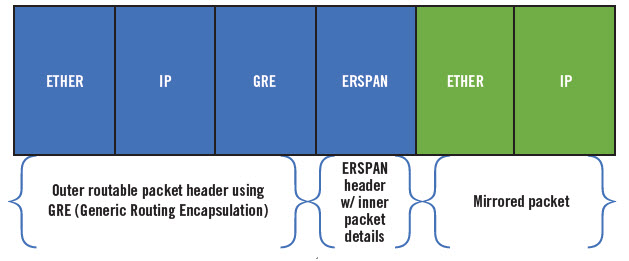
The Encapsulated Remote Switched Port Analyzer (ERSPAN) approach works like this: Computers and appliances mirror traffic on source ports and deliver the mirrored traffic to destination ports on another switch. The network traffic is encapsulated using Generic Routing Encapsulation (GRE) so that it becomes routable across a Layer 3 network as shown in the diagram below:
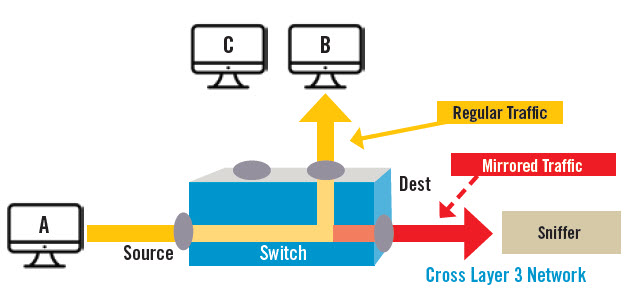
Cross Layer 3 Network
In this example of port mirroring, Host A sends traffic to Host B. A copy of the traffic is sent to the Sniffer, which is located in another (Layer 3) network segment. The ability to instantly deliver network traffic data to the remote network segment for analysis is a key ERSPAN feature that improves network security capabilities.
The use cases for ERSPAN include the analysis, diagnosis, and detection of malicious network traffic. The transfer of mirrored port data using Layer 3 protocols provides the network administrators and the InfoSec team with several options. They can: 1) Analyze the traffic offline in near real-time using deep packet inspection tools; 2) Extract metadata from the packet headers, thus reducing scaling issues; and 3) Route the traffic to long-term storage to preserve a record of network activity for future forensic analysis.
The application of GRE to encapsulate mirrored packet data is shown in the diagram above.
The ability to route mirrored packet data using Layer 3 protocols is extremely helpful to the InfoSec Team tasked with monitoring the network for malicious activity. The reality is that the sheer volume of network traffic makes 100% real-time monitoring cost prohibitive. So it is critical to mirror, capture, and store port traffic it for future analysis. ERSPAN technology meets this need by providing both encapsulation and Layer 3 routing capabilities.
The implementation of ERSPAN enabled in Cloud environments with hundreds of virtual machines provides the InfoSec team with yet another tool to detect and identify unauthorized behavior on corporate networks.[/glossary_exclude]
recent posts
You may already have a formal Data Governance program in […]