It’s In The Journey
We have seen several iterations of the “Internet of X” mantra over the years: The Internet of Content, the Internet of Commerce, and the Internet of People.
The most recent iteration and arguably the most significant one is the Internet of Things (IoT). Recognized as one of the key enablers for digital transformation, IoT describes the collective ability to configure sensors on things (1) in order to capture operational data, exploit that data, gain insight about the operation of these things, control them, alter their behavior, and ultimately produce “better outcomes.” (2)
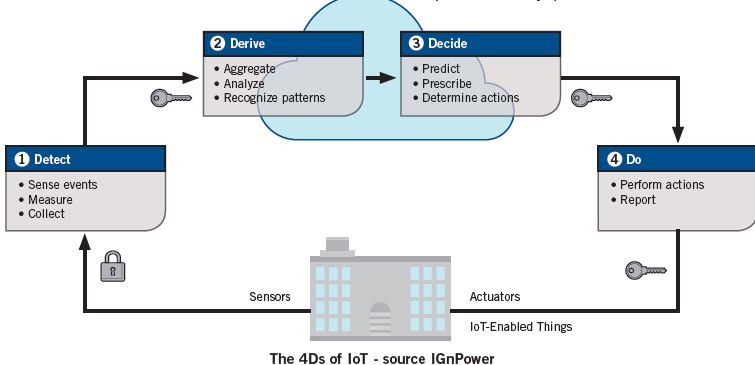
Although IoT systems tend to be architecturally complex, the overall principle of their operation is consistent. You Detect, you Derive, you Decide, then you Do.
As an Information Governance professional, I classify IoT data as corporate data that must be governed in accordance with legal and regulatory obligations and internal corporate policies.
However, as an IoT professional, I would say, yes but not so fast.
This article will introduce the term IoT Trustworthiness, an emerging domain that overlaps with IG in some areas, but is potentially much more significant to the organization.
This article is thus a call to action to both IoT practitioners and IG professionals.
- IoT practitioners should heed the growing governance debt that will inevitably result from the exponential growth of IoT data volumes
- IG professionals should watch out for that incoming train called IoT and recognize the important role they are destined to play in IoT Trustworthiness
Most people associate the term IoT with consumer-oriented devices like home thermostats. But it is in industry (3) that IoT applications have the most impact. In the last few years, the number of IoT sensors has grown exponentially. (4) By 2020 that number is expected to exceed 20 billion. This means that IoT systems are destined to generate volumes of data that will dwarf the volumes of data and information generated by business systems.
Governing the IoT Data
As already stated, data produced and consumed by IoT systems should be considered as corporate data that is subject to governance controls mandated by laws, regulations, standards, and eDiscovery rules, as well as rules defined by internal policies.
Adopters of IoT solutions face a wide range of technical and organizational challenges: how to cope with fast evolving technology and architecture, how to deal with the challenges of integration, and above all, reconcile IT with Operational technology (OT) (5) issues and manage their convergence.
As IoT solutions continue to expand and mature, the volume of IoT data generated by the sensors will witness exponential growth. Organizations will need to address several fundamental questions:
- What is the IoT data and who owns it?
- What are the rights of the IoT solution adopters?
- What are the obligations of the IoT solution providers (6) towards this data?
- What are the Data Protection best practices for this data?
- How long should this data be retained?
- How to deal with issues like data lineage and data residency?
Throughout my years in the IG space, I have always been struck by the years of inaction of organizations vis-à-vis their mounting IG debt and the uphill battles IG practitioners continue to face in getting their initiatives off the ground.
There is no question in my mind that the governance of IoT data will face similar challenges. But these challenges will be more complex, however, due to the physical nature of these systems.
I will get into these challenges in the next section, but let me first get the “good news” out of the way:
- a) Governance debt for IoT data is still very low: Most IoT systems have been in production for a relatively short period of time. This means that the volume of IoT data is relatively low and the governance debt for the IoT data is still low. No time to waste here however, since the volume of IoT data is about to explode.
- b) IoT data is structured and well organized: It should not be difficult to identify this data, classify it and define governance rules for it. Adding governance frameworks to existing IoT systems to actually enforce the governance controls will require engineering efforts, but it is doable.
IoT Trustworthiness
The discussion about governing IoT data CANNOT be limited to data only. This is due to a very simple fact about IoT: IoT is much more than IT for Things.
By definition, IoT systems have a digital side and a physical side. The governance of the IT aspects of these IoT systems (security and privacy) cannot be separated from the governance of the OT aspects of these systems (safety, reliability and resilience).
Enter the term: IoT Trustworthiness.
The Boston-based Industrial Internet Consortium or IIC (7) defines IoT Trustworthiness as follows:
It is the degree of confidence one has that the system performs as expected with characteristics including safety, security, privacy, reliability and resilience in the face of environmental disturbances, human errors, system faults and attacks.
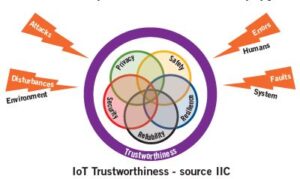
Establishing and maintaining the trustworthiness objectives in an IoT system leads to better outcomes, such as a better alignment with the corporate business objectives, a better visibility of operational risks, etc. On the other hand, failure to achieve and maintain the trustworthiness objectives can lead to significant negative consequences, such as serious accidents, equipment failures, data breaches, and operational interruptions to name a few.
Note: In so many IoT use cases, issues like safety and security far outweigh traditional IG concerns. For example, delaying a security patch in order not to affect production may introduce safety risks which can lead to serious accidents where people may be physically harmed. The issues and choices that IG Professionals face in projects like shared drive clean-up of ROT (8) pale in comparison. Nobody was ever injured by duplicated documents in a shared drive.
In order to assess the overall trustworthiness state of an IoT system, one must look at the state of each of the IoT Trustworthiness characteristics: Security, Safety, Reliability, Resilience and Privacy.
For example, the Current state of one characteristic may fall short of the Minimum level mandated by laws and regulations for that characteristic. On the other hand, the Current state of another characteristic may meet the Minimum level but fall short of the Target level set at a corporate level.
Below is a description of these Current, Minimum and
Target states:
- Current State (red): This is the “trustworthiness” status of the IoT system, based on how it is currently designed, implemented and operating.
- Minimum State (blue): This is a non-negotiable trustworthiness level mandated by external authorities and parties, example legal, regulatory, standards, and industry best practices.
- Target State (green): This trustworthiness level exceeds the Minimum state, and is based on internally-defined and self-imposed drivers and objectives (business and technical).
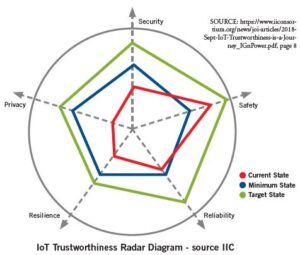
The “radar map” in the diagram below provides an example of the IoT Trustworthiness states of a system. In this example, Safety exceeds the mandated minimum legal requirements while the other characteristics (Security, Reliability, Resilience and Privacy) fall short of their respective mandated minimums and thus require efforts to become compliant.
This visual view of IoT Trustworthiness will help the organization understand its current situation vis-à-vis the trustworthiness of IoT system and prioritize the work needed to become compliant.
INFORMATION GOVERNANCE VERSUS IOT TRUSTWORTHINESS
Readers who have been trained in the art of Information Governance should have recognized by now that IG and IoT
Trustworthiness share some similarities:
- a) IoT Trustworthiness may be complex as a topic, but at the end of the day IoT data is corporate data that must be governed. This data must be classified, its lifecycle managed and its eDiscovery properly handled in case of litigation.
- b) Like IG, IoT Trustworthiness is a multi-faceted discipline that requires a collaboration between multiple groups in the organization.
- c) Just like IG, IoT Trustworthiness needs a leader9 who is empowered10 to drive the trustworthiness efforts throughout the lifecycle of the IoT system.
IoT Trustworthiness is also different from IG. Its scope is much wider covering several well-established functions which have their own teams, long traditions and mandates. Safety plays a very prominent role in IoT and Cybersecurity plays a central and enabling role in IoT and beyond (safety, privacy, etc.)
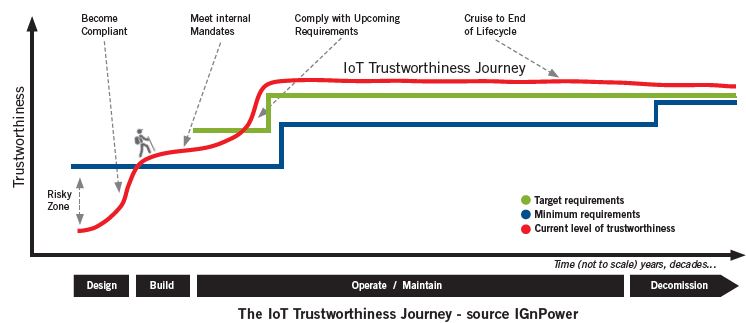
IoT Trustworthiness Journey
IoT systems tend to have long lifecycles. For example, the lifecycle of a manufacturing plant and its systems may be decades long:
- During this long lifecycle, some of the plant’s internal systems and sub-systems may be upgraded, IoT-enabled, or totally replaced
- IoT data produced and consumed by the plant’s systems may have long lifecycles
- Trustworthiness requirements for the system may change over time due to changes in laws and regulations or changes in the architecture of the system itself.
What all this means is that establishing and maintaining the system’s trustworthiness is not a project. It is an effort that must be sustained throughout the lifecycle journey of the system (diagram below):
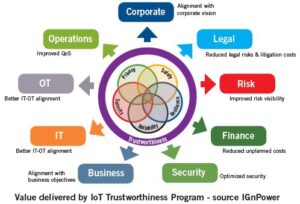
The IoT Trustworthiness journey must be piloted by a program that acts as a framework for organizing, directing, implementing and maintaining trustworthiness of an IoT system throughout its lifecycle, and in accordance with established Corporate Business Objectives.
Similar to the Information Governance program within the organization, the IoT Trustworthiness program must have a corporate sponsor to set the mandate and empower the organization to achieve that mandate, a program tsar to lead and manage the program, and a steering committee for the stakeholders who will coordinate the cross-functional implementation of the various facets of trustworthiness.
The program must also deliver real value to the organization in the form of “better outcomes”. This value must be communicated to the various groups and stakeholders in the organization in terms they relate to and understand.
A lot to unpack here and perhaps I should dedicate an article in the future to the subject of the IoT Trustworthiness Program, its structure and its activities.
Suffice it to say that a core component of the initial stages of this program is an assessment of the Current state of the IoT system and a determination of the Minimum state based on external drivers like laws and regulations, and the desired Target state based on internal drivers like corporate strategy.
IG professionals have an important role to play in this regard.
Conclusion
The trustworthiness of IoT systems and the governance of their IoT data are key to ensuring that these systems can deliver on their intended objectives. Both efforts should be maintained throughout the full lifecycle journey of the IoT systems and their IoT data.
There is little time to waste here as IoT technologies and architectures are evolving fast. AI and Distributed Ledger technologies like Blockchain are starting to play central roles within IoT systems. Issues like AI ethics (why did the AI make this versus that decision) and the seemingly irreconcilable conflicts between Blockchain and privacy (example GDPR’s Right-to-Forget) are getting to the forefront.
Terms like Safety-by-Design, Security-by- Design and Privacy-by-Design are not mere catchy buzzwords. They have a significant impact on the success of IoT systems and ultimately on the Digital Transformation strategies of organizations. These terms must be understood and the principles behind them weaved into the fabric of the IoT systems.
To close, I think it is safe to say that the need to govern IoT data is real and looming… it is also inescapable. But it is part of a wider conversation in which issues related to the trustworthiness of IoT systems will dominate the conversation.
Again, IG professionals will have an important role to play in all of this.[/glossary_exclude]
recent posts
You may already have a formal Data Governance program in […]