Stepping Into Security Assessments Part 1
Part 1, Selecting a framework
In today’s cyber threat landscape, companies have a fiduciary duty to assess their cyber security posture. This is the root function of a Cyber Security Assessment. Typically, 3rd party vendors are contracted to perform the Assessment. These firms have expertise in a variety of cyber security skills which they use to tailor the engagement to a scope appropriate for the organization being assessed.
One of the first steps when starting a Cybersecurity Assessment project is to select a framework. This choice will become part of the project requirements and in large part define the scope of work to be performed by the 3rd party vendor. There are several frameworks to choose from including: ISO 27001, COBIT, NIST Cybersecurity Framework, NIST 800-53, DOD 8570, DCID 6/3, HITRUST CSF and the Cloud Security Alliance’s – Cloud Controls Matrix. Even the Motion Picture Association of America has defined a cyber security framework to protect their member’s intellectual property.
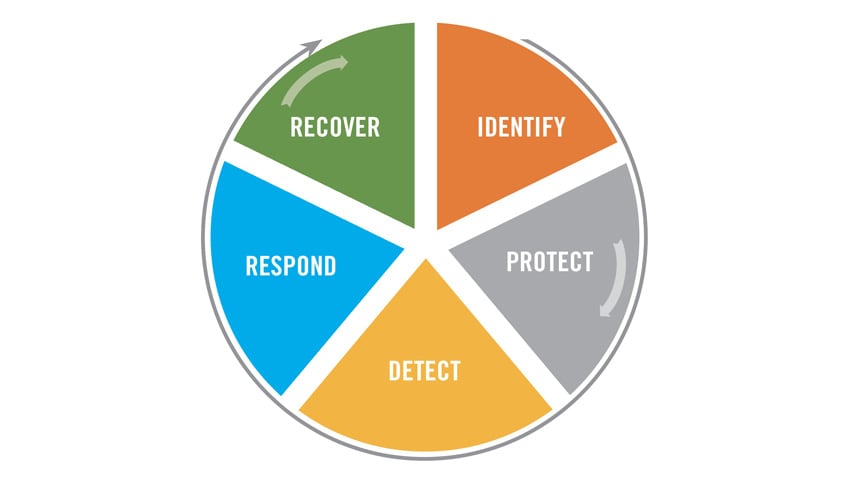
The NIST Cybersecurity Framework consists of five “functions”. The five functions are: Identify, Protect, Detect, Respond and Recover as shown below:
These five functions are sub-divided into 22 categories … and then each category has multiple controls. One issue with the NIST framework is that a comprehensive Security Assessment using this framework can quickly become a big project, often too big for the organization’s size.
For small and medium sized business, a good step forward is to specify the Center for Internet Security (CIS) Top 20 controls as the framework the independent cybersecurity team will assess. The CIS top twenty controls provide an easy to understand assessment tool which senior executives will understand.
Once the CIS controls are evaluated, the organization’s security posture can be easily visualized using color-coded infographics and risk score heat charts. Many Security Assessments include an evaluation of the business’ people, processes, and technologies. There is no point in spending technology dollars if the existing corporate processes do not support their use. These decisions can be explored using Radar charts to visualize the cyber readiness of three metrics: people, process, and technology. Radar charts depict cyber security assessment scores in a circular chart with gradient ranking that shows executives the information they need to act on to enhance their security posture.
The second step in the Cyber Framework series will explore assessment metrics and executive engagement.

recent posts
You may already have a formal Data Governance program in [...]