Protecting IoT Data Throughout the Digital Transformation Journey
[glossary_exclude]OVERVIEW
Being an Information Governance (IG) professional and an Internet of Things (IoT) professional, I tend to write about governance issues in relation to IoT. In this article I would like to provide an overview of the important term data protection within an IoT context, how data protection impacts digital transformation, and discuss the role of IG professionals in this regard.
This article comes with a warning to the reader. It contains several important (1) terms and acronyms that IG professionals should familiarize themselves with. Without doing so, you may not understand crucial points.
IOT
IoT is defined as:
- The ability to configure sensors on things in order to capture operational data,
- Exploiting that data by gaining insight about the operation of these things, and then
- Controlling and altering the behavior of these things.
Ultimately it is about producing “better outcomes” in terms of new business models, enhanced productivity, and reduced downtime. This is a mouthful of a definition. However, the concept of IoT is straightforward: you Detect, you Derive, you Decide, and then you Do.
We are witnessing an explosion of IoT solutions (2), yet most people outside of the tech sector are unaware of this; an explosion sometimes hidden from the untrained eye. The arrival of 5G and artificial intelligence (AI), and their fusion (3) into IoT, will lead to hyper-connectivity and exponential growth in the number, scope, and adoption rates of IoT solutions. This will transform the world as we know it.
The explosion of IoT solutions is also leading to an exponential growth in the volume of IoT data (audio, video, sensor readings, etc.) produced, stored, consumed, and exchanged. This volume of data is expected to surpass the data volumes accumulated in our business systems. This data needs protection and governance throughout its lifecycle, and some of it needs to be forensically preserved for legal and regulatory purposes.
DATA PROTECTION IN IOT
Let me switch gears to data protection. I am active within the Boston-based Industrial Internet Consortium® (IIC). This is a community of IoT vendors and organizations who represent the ‘Who’s Who’ in the IoT industry. Over the past few months, I have worked with a talented team of security experts from prominent IoT product and service providers to produce a whitepaper titled Data Protection Best Practices. (4) The paper was recently published and is getting very positive feedback from the market. Stacey on IoT called it a “great read.” (5)
When we started working on the paper, I asked the team whether there was an industry-wide definition of the term data protection. Market perception among my security colleagues is that data protection and data security are synonymous.
But if this is the case, why have two terms? There must be more to it.
A week later I attended a conference on data privacy where Dr. Ann Cavoukian, one of the world’s authorities on data privacy, was the keynote speaker. I asked her to define data protection. Her answer was unequivocal “this term means data privacy… the D and the P in GDPR stand for Data Protection.”
For our paper, we decided to use the term data protection as an umbrella term that covers several adjacent domains: data security, data integrity, data privacy, data confidentiality, data lifecycle management, data residency, etc. These domains are well defined in the industry with established procedures and best practices. These domains can also overlap and be interdependent on each other. We described the best practices for these domains at 5,000 ft level, covering the three main states that data can exist in: data in motion, data at rest, and data in use.
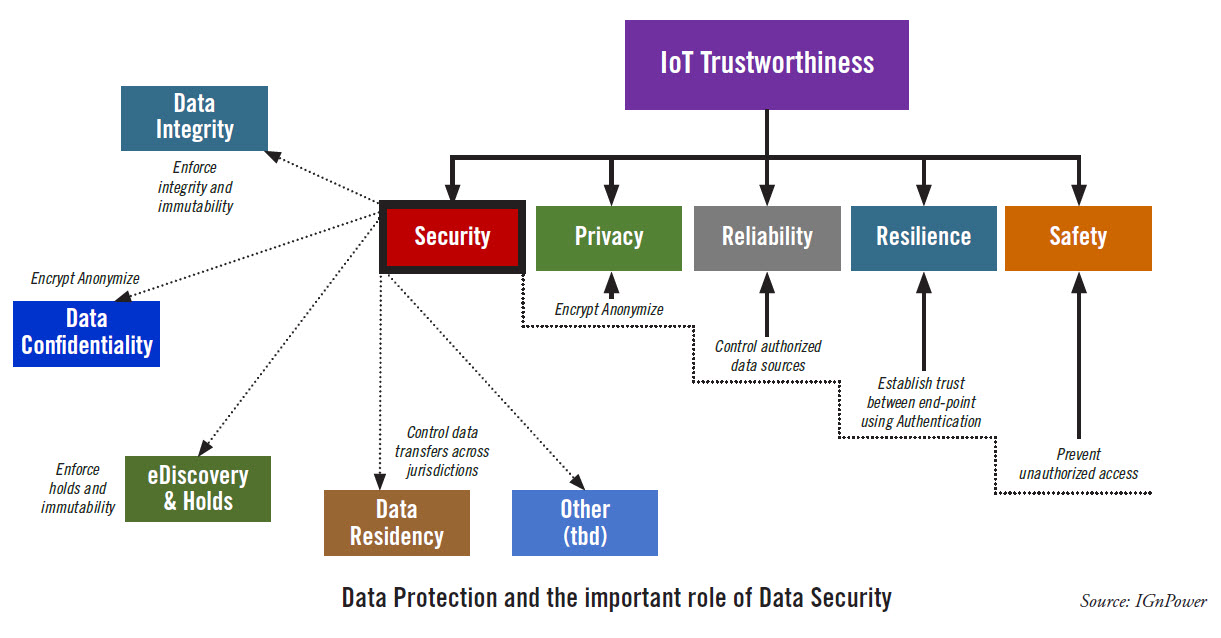
The diagram which appears as the featured images illustrates this approach. Two important points to highlight in this diagram (IoT context):
- Data security plays a central and enabling role in data protection
- Data security plays a critical role in domains that are normally associated with the physical world: safety, reliability, and resilience of IoT systems. Failure to apply appropriate data security measures can lead to serious consequences:
-Service disruptions that affect the bottom-line
-Serious industrial accidents that can lead to life-threatening injuries and environmental damage
-Major data leaks that can result in significant losses, heavy regulatory fines, loss of IP, and negative impact on brand reputation
IMPACT OF DATA PROTECTION ON DIGITAL TRANSFORMATION
Now let us talk about Digital Transformation. But, let me first cover two related terms. Digitization is the process of making information available and accessible in digital format and Digitalization is the process of applying digitized information to simplify operations. Digitization and Digitalization are prerequisites to Digital Transformation. (source: SAS)
On the IoT side, Industrial Digital Transformation (IDX) is often a “do or face extinction proposition.” It is a Caterpillar to Butterfly transformation and NOT a Caterpillar to Better Caterpillar evolution. It is the realignment associated with the application of digital technologies towards business and industrial models and processes, for the purpose of producing better outcomes.
The diagram below sums up this definition at a 10,000 ft level: Internal and external drivers are compelling organizations to transform the way they operate and ultimately bring about significantly better outcomes. This is done by applying three types of change factors: Business, Technology, and Governance factors.
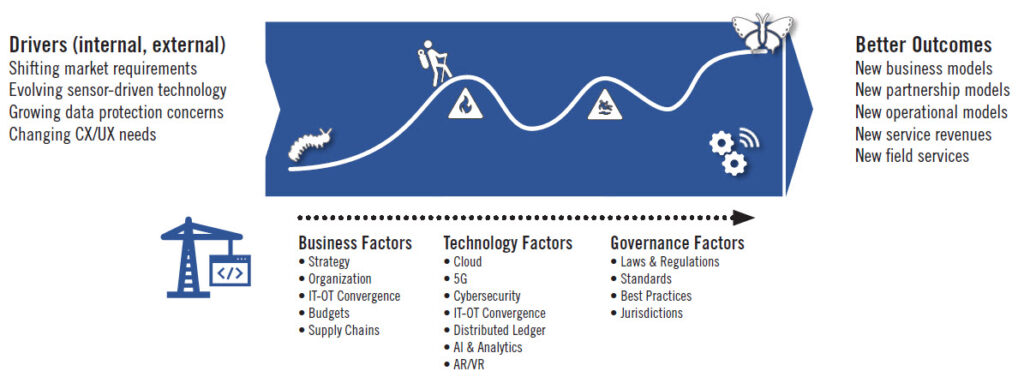
IoT is one of the key enablers of IDX. Throughout their IDX journeys, organizations across the IoT solution supply chain (6) must first assess the current levels and states of trustworthiness (security, privacy, reliability, resilience, and safety) of their IoT systems; second, define the corresponding minimum and mandatory levels of compliance; and third, develop and execute strategies for achieving and sustaining compliance with the minimum IoT Trustworthiness requirements throughout the IDX journey.
THOMAS SIEBEL ON DIGITAL TRANSFORMATION
The technical name for IoT–cyber physical systems–describes the convergence and control of physical infrastructure by computers. We see IoT everywhere––connecting devices in value chains across industry and infrastructure and generating terabytes of data every day. (7)
Data produced, stored, consumed, and exchanged by IoT systems MUST be protected (in motion, at rest, and in use) This protection must be applied throughout the IDX Journey and beyond. Failure to do so can lead to serious disruptions and interruptions in that journey, putting in question the ability of the organization to achieve the intended better outcomes within the set timelines and budgets.
CONCLUSION
Protecting IoT data throughout the Industrial Digital Transformation journey is key to the success of that journey. Data protection strategies must be designed to mitigate multiple types of risks to data in all their states: at rest, in motion, and in use. Failure to do so can lead to serious consequences for IoT systems, such as service disruptions, serious industrial accidents and personal harm, loss of IP, regulatory fines, and negative impact on brand reputation. This requires the active engagement of the Business, Operations, CIO, CISO, and CDO organizations.
The governance of the IoT data overlaps with and in some cases can be an integral part of data protection efforts. Thus, IG Programs, which are typically focused on IT data, need to be aligned and perhaps integrated with data protection activities and processes. It behooves IG professionals to gain knowledge and understanding of IoT systems, the context of the IoT data that these systems produce, store, consume and exchange, and finally how they can contribute to the data protection efforts in the organization.[/glossary_exclude]
recent posts
You may already have a formal Data Governance program in [...]